I’m trying something different this month. I’ve decided to write about something which is not about finance. Instead it’s about my experience and frustrations trying to write regular blog entries, and some topics about data security.
I put some effort into writing thoughtful articles with original material and personal perspectives. Partly it’s an opportunity to find a creative outlet and an excuse to research and write about things I find interesting. In my own way and style. I know my writings aren’t to everyone’s taste. That’s ok, but it would give me great joy to know that people enjoy reading my work, and of course if no-one knows the articles are there, no-one will read them! So I do some basic marketing.
MailChimp and Generic Concrete Cheese
In addition to publishing links on LinkedIn each time a article is published, I run a small e-mail subscription database on MailChimp. That’s the little sign-up box at the bottom of each article. This is, as I’ve discovered, a double edged sword. On the one hand, I want people to find my material when I put the effort into writing. On the other hand, whenever you put anything on the internet, some Pirates will always abuse it and ruin everything. Make it hacker-proof and no-one can get through the multiple sign-up steps to prove they’re not a robot. Make it too easy and the only names on your signup sheet remind me of the sign-up sheets we used to put up for events at university. Names like Phil McCrack, Ivana Huggenkiss and Ben Dover (and other amusing made-up names) appear where you hoped to find real interest. My MailChimp account was no different.
After a couple of weeks I realised that I need to have a look before trusting the system and whilst bots have less imagination and humour than university students, the result was not too different. I basically had to look at the names and email addresses and see if they made sense. So if I went too far and deleted you, I apologise, and compliment you on your interesting name, Ms N. E. Generic Concrete Cheese (yes really) and wonder why you don’t use your name in your email address. Frustrating! And it makes me a spammer to the random email accounts that were subscribed, which is also not fair, and gives me a bad reputation.
Basically, Internet security is a must these days. With all the data that we hold online, or our computers, there is no way around it. We must be smarter about the way that we store data, and the people and things we allowed to access it. I’ve set out some examples below of where we all have to be so incredibly careful these days.
Microsoft’s spontaneous customer service
Only today, I picked up the phone to be told that the nice lady who was calling me was calling (spontaneously) from Microsoft. She wanted to warn me that they had detected malware on my computer and calling because my name (which she didn’t know) was on their database and they wanted to make sure that they helped me clean it up. I was already somewhat suspicious, because the telephone number that called me was from somewhere in the UK. I’m in Switzerland…

I have heard about this scam for some time. In fact I’ve warned my family not to entertain these calls for very long. I just worry that they might call someone like my parents or people from an (even) older generation, and they might be gullible enough to actually give these people access to their computer and allow them to start stealing data. It makes me sad, that there are people out there who effectively have a paid job which is stealing other peoples data.
I should probably add that I was in a mischievous mood when I got the call, and it’s not the first time I’ve had this call, so I strung them along a bit about how clever they were to notice the problem I didn’t even notice, before telling them I only have a mac and hanging up.
My teenage son, who is much better with computers than me (isn’t that often the way?) suggested that next time we get a call like that we “set up a virtual computer” on my computer, that’s fake and totally contained and let them access that and get frustrated, but it’s just too much effort for me. I just want to get on with my life. Also, I’d be playing with fire…I’d probably do it wrong and give them exactly the access they were trying to get by trying to be too clever. No thanks.
Stolen passwords are valuable (because we’re all lazy)
In fact, stealing data seems to be fairly big business. Some years ago, I received an email from LinkedIn telling me that my password had been compromised. I suspect, like many others, the password that I used for LinkedIn was the same as quite a few other services. This was quite a big inconvenience. However, I’m glad I changed all of my passwords and even though it’s in pain to try and remember every single different password I have on every different service (there are quite a lot), I realised the hackers have become simply far too sophisticated, in fact probably far more sophisticated than I am. I now regularly have to reset a password because I no longer have any idea which one I used for what…
In fact, of over 100 million passwords stolen from LinkedIn in 2012, an article on TechRepublic suggests that about a third of these were passwords that were either previously compromised, or were on a list of “frequently used passwords” (like 123456, or “password” – seriously over 140,000 users were using that one).

Scarily, hackers have started packaging together list of cracked usernames and passwords from a number of different large scale hacks over the last few years are available for sale on the black market, according to this 2016 article on vice.com for 5 Bitcoin (about USD 2,200 back in 2016, although now 5 Bitcoin is worth a whopping USD 84,000!) or may even available for free by now according to this 2019 article on wired.com, because they have been available to, and exchange between hackers for so long. Either way it’s bad news for us users. So, basically, if you’re still using your pre-2012 LinkedIn password for other websites, it’s really about time you changed it.
Do yourself a favour and at least check haveibeenpwned.com to see if your email address or username has been compromised.
Hacking attempts
Before setting up my own blog, I had spent many happy hours designing and publishing my wife’s business website (and two others, long before, written in html code, which I can now barely remember).
Every so often, like a nervous gardener checking to see if a seedling was growing, I’d try and figure out how to access the site statistics – maybe lots of people were already being convinced about my wife’s professional charm, obvious professional abilities and broad appeal, obviously made all the more impressive by her fancy new website(!), and appointments would start streaming in.
When I finally found the statistics I was stunned at the results.
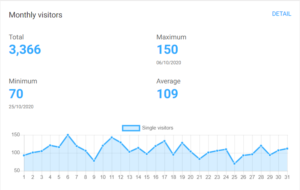
Here is a snapshot of the total visitors to my wife’s site last month, to give you an idea of what I saw. These numbers (70-150 visitors per day) are about typical, maybe a bit low, but at first glance it was highly suggestive that I’d done a stand-up job of positioning my wife’s services perfectly on the internet.
On the one hand excited, and on the other somewhat suspicious. Were there really that many people looking at the site? Why? I soon figured out that most of the visits looked a little fishy. My excitement quickly turned to disappointment and then I started to get nervous when I saw the geographical spread of the visitors.
Surely not that many people in Russia, China and Latvia could be that interested in getting personal coaching and alternative therapies in German!
Curious as to why my tax and personal blog and my wife’s small business would be so popular I looked for other statistics. This shows the number of people that actually went to an actual page on the site. Rather than the astonishing numbers in the visual above, the real number of visitors is much more modest, which is slightly disappointing but probably more likely to be true.
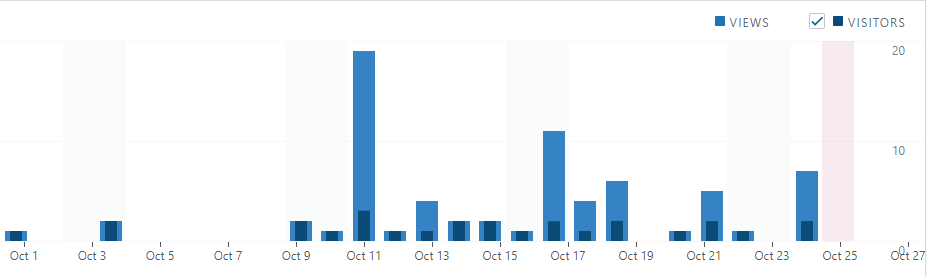
What’s interesting is the statistics for the visitors not going to the pages we want people to see. What are they doing? Where are they going if they’re not landing on the website’s pages? Basically they’re trying to find backdoors and other sneaky ways to hack the site and insert content or take control of it.
I soon started to use Wordfence to protect both sites after noticing all the dodgy of site visits from suspicious countries, which seemed odd to me, for a local personal services website.
Here is a sample of the visitors for my wife’s site which were automatically blocked, either for trying to exploit a weakness, or by trying random login combinations to access the site. Skip past this bit if you’re not interested in the detail, but I’m setting out below the visitors we had one week in the summer:
| Country | Total IPs Blocked | Block Count |
|---|---|---|
| Sri Lanka | 6 | 40 |
| Germany | 13 | 14 |
| France | 5 | 7 |
| Switzerland | 3 | 3 |
| Denmark | 1 | 2 |
| Canada | 1 | 1 |
| Sweden | 1 | 1 |
| Singapore | 1 | 1 |
| United States | 1 | 1 |
| Japan | 1 | 1 |
It’s crazy really, and also actually kind of annoying to have to defend my sites from hacking attempts all the time, in my spare time, and I’m glad I can rely on WordFence to do most of the heavy lifting. However, I still worry that something slipped through.
My own site (this one) has only been up and running since Summer 2020, it’s not the key to a large business with customer information or credit card details, so there’s no obvious financial gain to be had in hacking my site, yet still it’s getting attacked multiple times per day.
So what’s in it for them?
Puzzled as to why our sites should be such an interesting target for hackers, I found a really good article setting out the main motivations of hacking wordpress sites, which for most people represent a hobby or a small business.
Reasons Why Hackers Hack WordPress Sites – MalCare
In short, and to summarise the article, the main reasons are:
- Storing files on my website that shouldn’t be there (e.g. pharmacy product links), so, to make marketing referrals
- Taking over my site to use it to spam people (with either phishing attacks to get their data or sell them personal products they probably don’t need)
- For kudos, pure and simple
- To access any information that might be on my server that I choose not to show (not really the case on small business sites)
For me, it’s just a huge irritant. Spamming and hacking mean I get stupid numbers of visitors to my site and I have to stay alert with my web security, updating all the little mini-programs that give the site its functionality every time there’s a security update (and I have to say, there are updates issued quite often).
Privacy is great, but where are my emails...?
Because I refuse to use one of the big “free” e-mail providers like Google and Hotmail (because I value my privacy) I run my own Swiss-hosted email server. Also it was kind of fun to choose my own email address and domain.
However, pretty much all accounts can be hacked by guessing the username and password, and, my email account was no different one day in August 2019 – something I noticed just because one day there were suddenly no emails in my inbox, or anywhere else, for that matter, only a few hours before I had all my emails there. Sadly, probably another legacy of the linkedin hack.
I contacted my provider to find out what could have happened (accident, technical failure or malicious act by someone else) and was told that, for data protection reasons, the ISP couldn’t give me the IP number of the computer which accessed my account without a cooperation order from the police. Oh, the irony…
At this point I’m rather feeling like a target. The last in a series of quite annoying attacks on me personally. I probably shouldn’t take it so personally, but things like this cause me great inconvenience, even though I realise I’m almost definitely not alone in being targeted.
I guess I can see that any information is valuable to someone, and a scrape of my emails could yield information about where I bank, and if I’m not careful, I might have emailed myself passwords for online shopping and finance sites which could be monetised at my expense. Or give clues to other things that could be attacked. It’s a dark world. I changed all my passwords immediately anyway. Again. So annoying.
Phishing attempts and the consequences of success
However, large organisations have to be so careful not to either lose access to their data, or access to their systems. I work for a bank. We have regular education and phishing simulation tests (as well as pretty sophisticated firewalls and other internet restrictions and monitoring) to protect our clients’ data and our own systems.
Some people aren’t so lucky. I like to run and stay active, and I like running tech, so I noticed immediately when Garmin’s systems were suddenly unavailable for several days during July 2020. A number of articles written near the time suggested this was a ransomware attack, including this article from Cyber Security Hub, one of many which reminds people that phishing attacks can result in the corporate computer system being shut down by hackers, often needing a significant ransom to be paid to unlock the data and get back to business. Given US criminal sanctions on the payment of ransoms, Garmin has been tight-lipped about how it resolved its IT issue. Such schemes are immediately profitable for hackers. They provide an immediate financial reward if the victim pays up.
The perhaps better-known alternative is data theft, for example the hack on the Bulgarian tax administration which I mentioned in my first blog article where tax and personal data of 5 million people tax payers were stolen and published online for public access. Perhaps the motivations here were more ideological, but no less harmful for the people whose private information was leaked. For me, another reminder that less is more, and (with international tax data exchange in mind) another prompt to consider how safe it is to pool and exchange massive sets of very personal information. Is the benefit worth the risk?
So, what are the takeaways?
Firstly, this is mainly a rant because I’m frustrated at feeling attacked all the time by scammers, but I wanted to share some of the many and varied ways internet criminals are trying to hijack our accounts to make money, somehow.
So, with this in mind, and hoping that I, and others, can learn from the mistakes of the past:
- Passwords – Don’t use the same password for everything (no matter how tempting). Only one site needs to be hacked and then you might be sharing more information that you thought, across other accounts with the same or similar combinations (yes, hackers can add a 1 to the end of your password as well).
- Be careful where you click – spam is not harmless, things that sound too god to be true often are, and clicking on the wrong link can give bad guys control of your complete computer.
- Keep backups – some things you can’t defend against, no matter how hard you try, so make sure you have a copy of everything that’s important to you in case you (or someone else) deletes it all for you. (check with your mail provider how long they retain deleted mails, and keep important personal stuff from your computer on an online or offline secure storage).
Finally, on a lighter note, here’s a link to a sketch I really enjoyed, and I hope you will too:
Thanks for reading!
Until next time,
– PhilG

Thank you, next please!
If you’re worried about missing the next article, please let me have your details and you can be one of the first to find out! There might be a couple of extra steps whilst I try to keep out spammers. Sorry…
The mailing list is hosted on Mailchimp and only used for sending new article alerts. You can unsubscribe at any time.